howtos:encrypted_usb_storage
Start out by identifying your device name. Insert the usb stick and run in a terminal:
dmesg
The output would be something like this:
........ ........ [17028.141759] usb-storage: device found at 20 [17028.141772] usb-storage: waiting for device to settle before scanning [17033.140314] usb-storage: device scan complete [17033.141276] scsi 9:0:0:0: Direct-Access Flash Disk 5.00 PQ: 0 ANSI: 2 [17033.185463] sd 9:0:0:0: [sdc] 1998848 512-byte hardware sectors (1023 MB) [17033.186669] sd 9:0:0:0: [sdc] Write Protect is off [17033.186682] sd 9:0:0:0: [sdc] Mode Sense: 0b 00 00 08 [17033.186688] sd 9:0:0:0: [sdc] Assuming drive cache: write through [17033.194505] sd 9:0:0:0: [sdc] 1998848 512-byte hardware sectors (1023 MB) [17033.196549] sd 9:0:0:0: [sdc] Write Protect is off [17033.196563] sd 9:0:0:0: [sdc] Mode Sense: 0b 00 00 08 [17033.196569] sd 9:0:0:0: [sdc] Assuming drive cache: write through [17033.197444] sdc: sdc1 [17033.199662] sd 9:0:0:0: [sdc] Attached SCSI removable disk [17033.200242] sd 9:0:0:0: Attached scsi generic sg3 type 0 ........ ........
This device is called /dev/sdc and the partition is sdc1.
Unmount the device so we can massage the partitions on it :)
Use whatever tool you like to format the stick into a ext3 partition. WARNING THIS WILL DELETE ALL DATA ON THE STICK!!
Install cryptsetup:
sudo apt-get install cryptsetup
Now create the encrypted partiton:
sudo luksformat -t ext3 /dev/sdc1 Creating encrypted device on /dev/sdc1... WARNING! ======== This will overwrite data on /dev/sdc1 irrevocably. Are you sure? (Type uppercase yes): YES Enter LUKS passphrase: Verify passphrase: Command successful. Please enter your passphrase again to verify it Enter LUKS passphrase: key slot 0 unlocked. Command successful. mke2fs 1.41.3 (12-Oct-2008) Filesystem label= OS type: Linux Block size=4096 (log=2) Fragment size=4096 (log=2) 62208 inodes, 248742 blocks 12437 blocks (5.00%) reserved for the super user First data block=0 Maximum filesystem blocks=255852544 8 block groups 32768 blocks per group, 32768 fragments per group 7776 inodes per group Superblock backups stored on blocks: 32768, 98304, 163840, 229376 Writing inode tables: done Creating journal (4096 blocks): done Writing superblocks and filesystem accounting information: done This filesystem will be automatically checked every 29 mounts or 180 days, whichever comes first. Use tune2fs -c or -i to override.
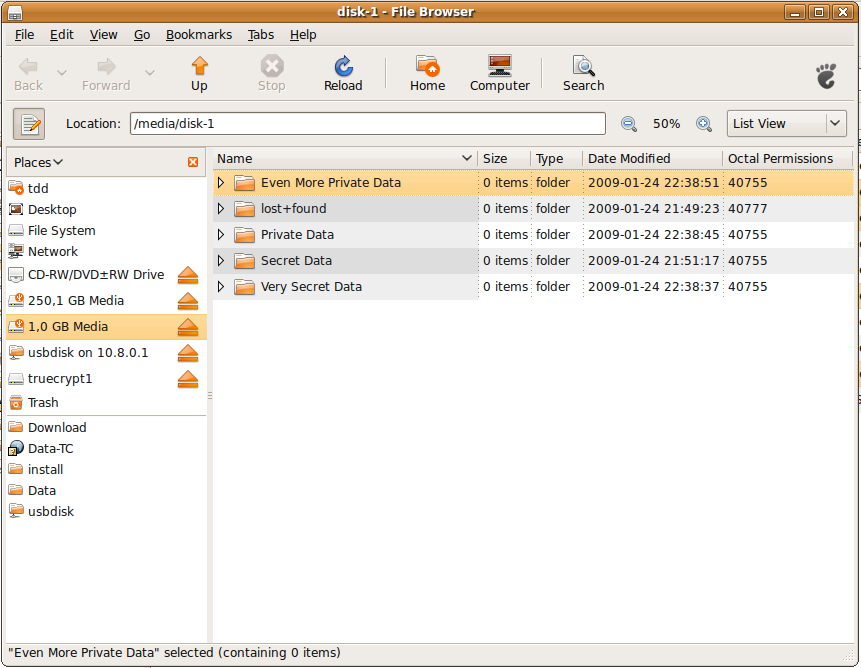
É voila you now have an encrypted usb stick. Now test it out by ejecting it and plug it back in:
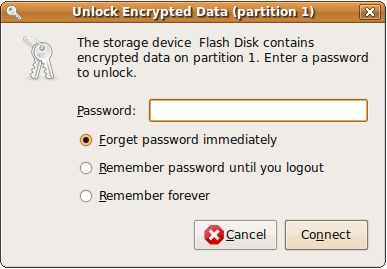
Enter your password and you should see it get mounted:
And do I have to remind you that if you loose the unlock password you will never recover your data on the stick....?? ;)
howtos/encrypted_usb_storage.txt · Last modified: 02/12/2018 21:34 by 127.0.0.1